- Cybersecurity is an important priority in the context of 5G development.
- The EU toolbox for 5G security is a set of robust and comprehensive measures for an EU-coordinated approach to secure 5G networks.
- This page provides a brief overview of the progress and efforts undertaken by MS with the 5G Toolbox implementation.
5G cybersecurity toolbox implementation
In January 2020, the NIS Cooperation Group which is formed of representatives of Member States, the Commission and ENISA (European Union Agency for Cybersecurity), published the EU toolbox of risk-mitigating measures. On the same date, the Commission adopted a Communication which endorsed the measures outlined in the Toolbox and underlined the importance of their implementation.
The Toolbox addresses cybersecurity risks outlined in the previously published EU coordinated risk assessment report. These risks can be largely categorised into four categories. These include:
- Local or global 5G network disruption (Availability);
- Spying on traffic/data in the 5G network infrastructure (Confidentiality);
- Modification or rerouting of the traffic/data in the 5G network infrastructure (Integrity and/or Confidentiality);
- Destruction or alteration of other digital infrastructures or information systems through the 5G networks (Integrity and/or Availability).
The Toolbox found a total of eight strategic measures that address these risks. In July 2020, the NIS Cooperation Group published a report that tracks Member States progress towards the EU Toolbox on 5G Security. Below you will find a summary of the eight strategic measures as well as an illustrative example from a Member State which was extracted from the progress report (if available):
- SM01 Strengthening the role of national authorities;
- Example – Estonia: In May 2020, the Estonian Parliament approved an amendment to the Electronic Communications Act. This amendment gives the government power to compel communication companies to provide information about the hardware and software used in their networks and to apply for authorisation to use the hardware and software of a network.
- SM02 Performing audits on operators and requiring information;
- Example – Austria: Following a new telecom regulation, MNOs operating a 5G network have to comply with information security measures and have to maintain an Information Security Management System (ISMS).
- SM03 Assessing the risk profile of suppliers and applying restrictions for suppliers considered to be high risk – including necessary exclusions to effectively mitigate risks- for key assets;
- Example – France: Key network assets are defined in the Order of 6 December 2019 and regulated as sensitive assets subject to control and authorisation before being rolled out. Those key assets include the radio access functions and most core network functions.
- SM04 Controlling the use of Managed Service Providers (MSPs) and equipment suppliers’ third line support;
- Example – Finland: MNOs are required to ensure that, in a state of emergency, critical systems and their guidance, maintenance and control can be returned to Finland without delay. The regulator, Traficom also has the power to issue regulations relating to network management.
- SM05 Ensuring the diversity of suppliers for individual MNOs through appropriate multi- vendor strategies;
- Example – Cyprus: The forthcoming regulatory framework will include guidelines for MNOs to develop and adopt appropriate multi-vendor strategies, using a risk-based approach.
- SM06 Strengthening the resilience at national level;
- Example – Spain: Diversification objectives at national level will be considered in the national 5G Strategy.
- SM07 Identifying key assets and fostering a diverse and sustainable 5G ecosystem in the EU;
- SM08 Maintaining and building diversity and EU capacities in future network technologies.
In addition, the report also outlined 11 technical measures and 10 targeted supporting actions that Member States can take.
Initial progress report
The Commission called on the Member States to take concrete steps to implement these recommendations and prepare a report on their implementation. In July 2020, the NIS Cooperation Group published this report. It is important to note that this report was published on the 29th of January 2020, and developments may have taken place since then. Furthermore, this report is based entirely on contributions from Member States.
Notable findings in the report include:
- A large majority of Member States are in the process of significantly strengthening national regulator powers (SM01).
- The implementation of measures aimed at minimising the exposure to high-risk suppliers (SM03) is ongoing in many Member States, however, there is uncertainty surrounding the timeframe for adopting this as it is a complex and sensitive matter.
- A significant number of Member States appear to have yet to review existing practices and adopt measures to limit the types of activity and conditions under which MNOs are able to outsource particular functions (SM04).
- Most Member States have not yet established or communicated clear plans to effectively address existing situations of dependency on high-risk suppliers and prevent future dependencies (SM05 and SM06).
In conclusion, the report found that a large number of Member States have already taken concrete steps to implement the various strategic measures. However, it also found that work is still ongoing in the Member States on defining the content and scope of the measures. Going forward, it recommends that Member States should intensify efforts to exchange information amongst each other to facilitate Toolbox implementation.
In the period after the publication of this report, the 5G Observatory has also independently observed some progress being made in the European Union. In particular, it found:
- In November 2021, the Irish Government announced its plan to use the EU 5G Security Toolbox as a framework for securing its 5G network. This will include legislation that will allow the Minister of the Environment, Climate and Communications to assess the risk profile of providers of electronic communications network equipment and, if required, to designate certain vendors as being high risk. The new legislation will be drafted in consultation with relevant Departments and Agencies, and a Regulatory Impact Assessment and consultation process will be conducted in early 2022.
- In December 2021, Estonia’s State assembly passed the new 5G cybersecurity regulations in an amendment of the country’s Electronic Communications Act. The law will now need to be approved by the president.
Second progress report
In June 2023, the NIS Cooperation Group published an updated report on MS progress in implementing the toolbox. As was the case in the previous progress report, its findings were based on contributions from MS about their progress.
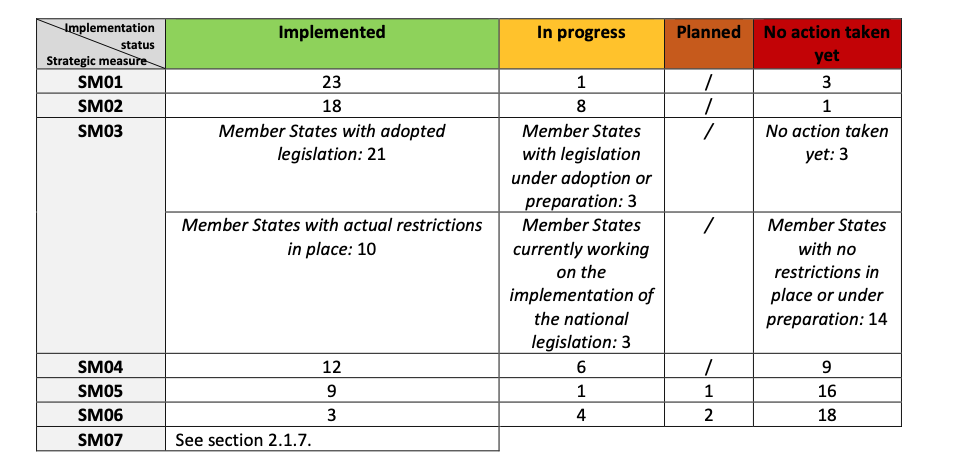
It found that measure “SM01 – Strengthening the role and powers of regulatory authorities” was the most widely adopted, having been actioned in 23/27 Member States. The progress of the other measures are as follows:
- SM02 – Performing audits on operators and requiring information
- 18 Member States reported having implemented SM02, while eight Member States reported the implementation to be in progress or planned.
- This is a significant increase from the first report, where only seven MS reported that this measure had been implemented.
- SM03 – Restrictions for high-risk suppliers
- 21 Member States reported having adopted legislation that gives national authorities powers to restrict high-risk suppliers and three have legislation under adoption or in preparation.
- SM04 – Controlling the use of MSPs and equipment suppliers’ third line support
- 18 Members States have either implemented or are in the process of implementing SM04.
- This is an increase since the first Progress Report, when five Member States considered this measure to be implemented.
- SM05 – Ensuring the diversity of suppliers for individual MNOs through appropriate multi-vendor strategies and avoiding dependency on high-risk suppliers
- 9 Member States reported having implemented SM05, while more than half of Member States have not.
- In the first progress report, only two MS reported that this measure was implemented.
- SM06 – Strengthening the resilience at national level
- Most Member States have no requirement to impose diversification at national level through an adequate balance of suppliers.
- Several MS reported that SM06 is difficult to implement because of the small size of their national market.
- SM07 – Screening of Foreign Direct Investment (FDI)
- By the end of 2021, 25 Member States either had a national FDI screening mechanism in place; adopted a new national FDI screening mechanism; amended an existing mechanism; or initiated a consultative or legislative process expected to result in the adoption of a new mechanism or amendments to an existing one











